Kraken customer data allegedly for sale on dark web

A dark web monitoring service recently flagged a listing for “panel access” to Kraken’s internal customer dashboard, potentially exposing the sensitive data of millions of crypto exchange users.
A screenshot of the alleged post from a Russian website itemizes an alarming quantity of personally identifiable information.
In dark web economies, panel access refers to compromised credentials used to login to internal customer support software like Zendesk or Salesforce or third-party portals like Kodex.
A placeholder fee of $1 indicates a desire to negotiate on price from the seller, ransomcharger. The authenticity of the listing is impossible to verify without accessing the dubious website via Tor and negotiating a purchase via encrypted messengers.
On occasion, sellers with low reputation scores fabricate listings to entice newcomers or gullible customers.
Moreover, government law enforcement officers regularly post fake listings on dark web marketplaces to lure criminals.
Despite widespread publication of the news, Kraken had not responded to the allegation on its X accounts, nor via its Telegram channel, as of publication time. Protos reached out to the exchange for comment but didn’t receive a response prior to publication.
After publication time, Kraken continued to investigate and responded. “We investigated the claims thoroughly and determined that the forum post is not legitimate and appears intended to mislead other forum users,” said Kraken’s Chief Security Officer Nick Percoco.
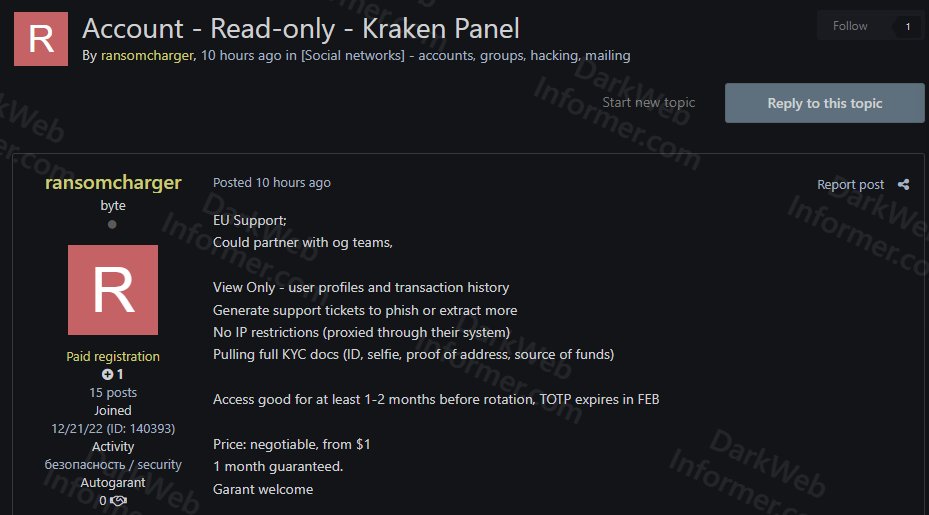
Screenshot likely from Russian forum
The screenshot is of a Russian-language dark web forum, likely Exploit or the Russian Anonymous MarketPlace (RAMP), which has shut down and respawned several times over the years under various names, including RAMP 2.0 and Exploit[dot]in (formerly Exploit[dot]biz).
Many dark web marketplaces are only accessible via a Tor browser.
There, a vendor is ostensibly advertising read-only access to Kraken’s know your customer (KYC) documentation, transaction histories, and support tickets. According to Kraken, the advertisement is for non-functional credentials.
Kraken is one of the world’s top 20 crypto exchanges and recently raised money from Citadel Securities at a $20 billion valuation.
Dark Web Informer, which claims credit for the news, has a sizable following on X and a mostly consistent history per the social media platform’s self-moderation tool, Community Notes.
A review of its 50 latest tweets returns no active Community Notes, excepting a single note that Dark Web Informer contested.
Read more: Verified Kraken and Binance accounts going cheap on the dark web
Although the panel as advertised wouldn’t allow withdrawals, i.e. direct draining of crypto wallets, the listing boasts capabilities that could be valuable for a social engineering or phishing campaign.
For example, the illegal credentials could display selfies, government IDs, crypto transactions, and source of funds declarations.
More critically, the vendor claims that its panel access allows creation of support tickets — a powerful tool used to feign credibility during a customer interaction.
Criminals ripping off criminals
If the listing is authentic, the read-only caveat is cold comfort. An attacker could open support tickets, or simply impersonate Kraken support with reassuring accuracy, referencing vast documentation to engineer a social engineering attack.
Kraken, as quoted above, denies that this attack vector was ever open.
The use of internal support tools to reassure a victim about the authenticity of a fake support agent’s identity before extracting money from their account has become a favored tactic for drainer hacks.
Any customer who receives a call from a company should be able to hang up and call the person back via the company’s official phone number.
Calling the company directly, using the phone number listed on the company’s own website, is a basic security step that shuts down many impersonation scams.
RAMP and its successors like Exploit have a hydra-like history of being taken offline by law enforcement only to respawn shortly thereafter. These forums are notoriously difficult to verify.
Scam listings are common, purposefully designed by criminals to rip off other criminals (a practice called “ripping”), as well as police luring criminals to demonstrate intent of criminal misconduct.
Edit 01:57 UTC, Jan 6: Added response from Kraken in eighth paragraph.
Got a tip? Send us an email securely via Protos Leaks. For more informed news, follow us on X, Bluesky, and Google News, or subscribe to our YouTube channel.
